How To Install Hashcat On Kali Linux
Hashcat manual: how to apply the plan for peachy passwords
In this manual, I highlighted the most basic steps of Hashcat using and detailed the master operating modes of the plan. This education is designed for absolute beginners. I hope it will reduce the number of 'children's' questions.
How to run and use hashcat (an instruction for hacking passwords)
Hashcat is a program for hacking passwords, information technology's a powerful application with lots of features.
Nevertheless, this is not the easiest to use program, therefore you demand to spend fourth dimension learning it. In this manual, the near typical situations with hashcat are described.
Nosotros will consider considered as very 'childish' questions, like 'how to run hashcat', and rather complex, like the right composition of masks, custom character sets, program options, trouble solving and then on.
The peculiarity of hashcat is the very high speed of animate being-force passwords, which is achieved through the simultaneous apply of all video cards, likewise as central processors in the system. It is possible to piece of work if several video cards or video adapters of different manufacturers are installed (for instance, AMD and NVIDIA).
When I click on hashcat.exe a blackness window flashes, and then disappears
Hashcat is a command-line utility. Then it does non have a graphical interface in the form of a familiar window. Therefore, Windows users may think that the program is launched in an unusual way.
To first the program, open the control window (or PowerShell). To exercise this, press Win+ten, and select Windows PowerShell:
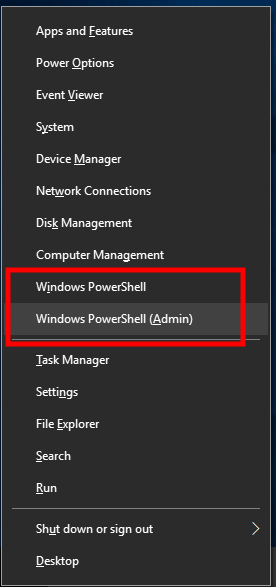
And so you tin act in 2 ways.
The outset option: you lot tin just drag-n-drop the executable file into the control window. The executable file is hashcat.exe or hashcat32.exe depending on your system.
The 2d option: on the command line, you tin can change the current working directory to the one where executable hashcat files are located. For example, my plan is located in the folder C:\Users\Alex\Downloads\hashcat-four.i.0\, to alter the current working binder, use the cd command, later which the folder to which you specify the desired folder, in my example the command looks similar this:
cd C:\Users\Alex\Downloads\hashcat-4.ane.0\
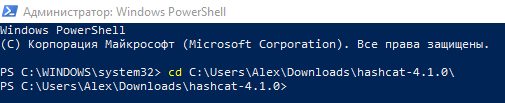
As you can see from the screenshot, the folder C:\WINDOWS\system32 is changed to C:\Users\Alex\Downloads\hashcat-4.ane.0.
Now to kickoff the program it is enough to type the proper name of the executable file indicating the current folder. The current folder is indicated by a period (.), So y'all need to put a backslash, it looks like this:
.\hashcat.exe
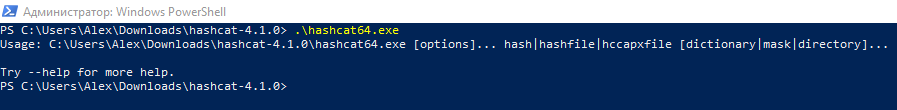
Since we did not enter any options, nothing happens, only a brief hint is displayed.
Throughout the didactics, nosotros will run the executable hashcat file with options. The simplest pick is -h, if yous write it, you will go a reference for using the program:
.\hashcat.exe -h
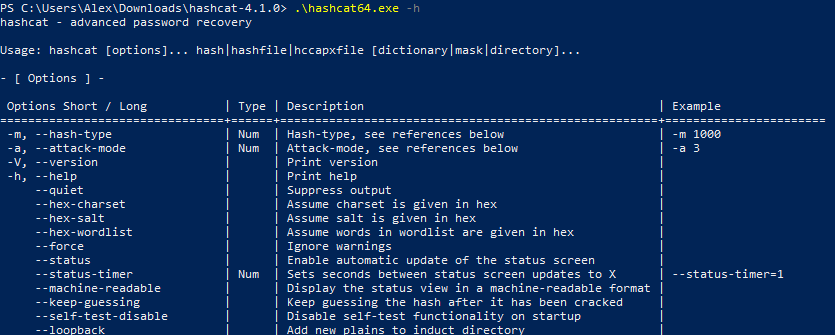
Download hashcat
Download hashcat from the official site by the link: https://hashcat.internet/hashcat/
Y'all will see:

The site has hashcat binaries and hashcat sources. The first is binary (executable) files, the second is the source lawmaking. We need binaries, i.e. hashcat binaries.
How to install hashcat
Hashcat does not require installation, since it is a portable programme. Information technology is plenty to unpack the downloaded archive. If you have problems with unpacking the .7z format, then use the program seven-Zip (archiver with a loftier compression ratio).
To run hashcat, it is necessary that the latest drivers for video cards are installed.
Drivers for hashcat
Notation: If you run Linux, and so run across the article "How to brute-force passwords using GPU and CPU in Linux" for instructions on installing the necessary drivers and packages.
The following graphics carte drivers are required:
- AMD graphics cards on Windows require AMD Radeon Adrenalin 2022 Edition (20.2.2 or later)
- Intel CPUs crave OpenCL Runtime for Intel Cadre and Intel Xeon Processors (16.1.ane or later)
- NVIDIA graphics cards crave NVIDIA Driver (440.64 or later) and CUDA Toolkit (9.0 or later)
Instal the NVIDIA commuter
Go to NVIDIA official website https://www.nvidia.com/Download/alphabetize.aspx, download and install the driver
Instal the CUDA Toolkit
Go to the official site https://developer.nvidia.com/cuda-downloads, download and install this toolkit.
Instal the Intel CPU video driver
Go to the official website https://www.intel.ru/content/world wide web/ru/ru/download/19344/intel-graphics-windows-dch-drivers.html, download and install the driver
Install OpenCL Runtime for Intel
Directly link to "Intel CPU Runtime for OpenCL Applications for Windows OS" on Intel website: https://registrationcenter-download.intel.com/akdlm/irc_nas/vcp/17773/w_opencl_runtime_p_2021.2.0.616.exe
See the commodity for details: How to install drivers for Hashcat on Windows
Hashcat options
Working with programs in the command-line interface is very different from working in the graphical user interface. In the GUI, nosotros press different buttons, move switches, etc. This is not the case with programs with a command-line interface. But at the same time the command line utility can have even greater capabilities than a similar program with a window interface. In order to control the functionality of console utilities, options are used.
In the output of the help you probably noticed a lot of data. This data is mostly devoted to the options.
Options are specified later on the file proper name separated by a space. Some options require specifying a sure value. Some are used without values (such options are besides called 'flags').
Options can be used one at a time or several at a time. With the help of options you can very accurately configure the program, use it at maximum chapters.
With i option we accept already met, it is the -h selection, which displays plan help, then we'll get acquainted with even more options and their possible values.
The next 1 is the -b option.
Running the hashcat criterion
The -b option starts the hashcat benchmark. This benchmark measures the speed at which passwords are checked.
Running the criterion will be successful merely if the drivers are installed correctly and everything is all right. Therefore, a benchmark is also a way to do a arrangement and hashcat check.
To run the creature-force speed check on the most popular algorithms on the command line blazon:
.\hashcat.exe -b
To stop prematurely, press CTRL+c. This shortcut stops all command-line utilities immediately. Recollect this combination!
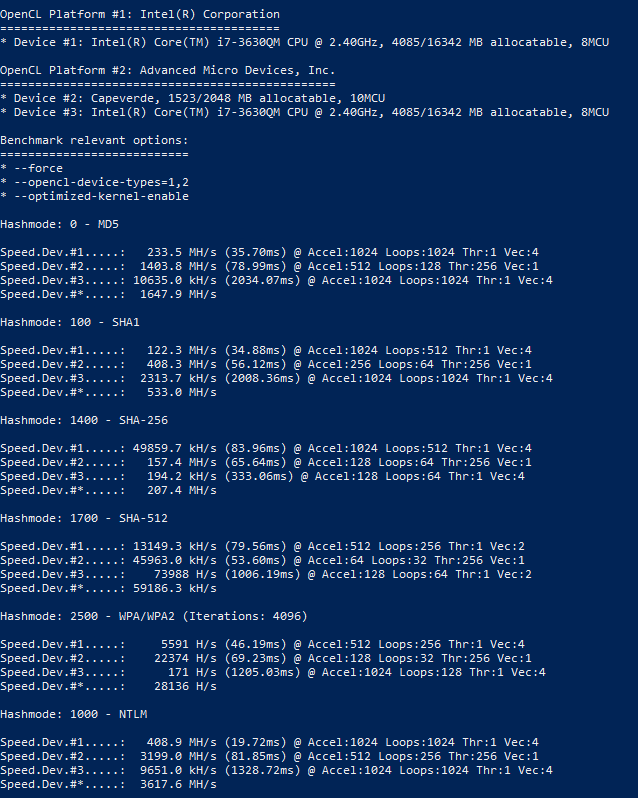
Speed is displayed for each device separately, as well as for all devices combined (line Speed.Dev.#*).
Instance:
Hashmode: 2500 - WPA/WPA2 (Iterations: 4096) Speed.Dev.#ane.....: 5591 H/s (46.19ms) @ Accel:512 Loops:256 Thr:i Vec:4 Speed.Dev.#2.....: 22374 H/s (69.23ms) @ Accel:128 Loops:32 Thr:256 Vec:1 Speed.Dev.#3.....: 171 H/s (1205.03ms) @ Accel:1024 Loops:128 Thr:1 Vec:four Speed.Dev.#*.....: 28136 H/s
Which device exactly corresponds a number is written at the very offset when the program is launched, for example:
OpenCL Platform #1: Intel(R) Corporation ======================================== * Device #1: Intel(R) Core(TM) i7-3630QM CPU @ 2.40GHz, 4085/16342 MB allocatable, 8MCU OpenCL Platform #two: Advanced Micro Devices, Inc. ================================================ * Device #2: Capeverde, 1523/2048 MB allocatable, 10MCU * Device #3: Intel(R) Core(TM) i7-3630QM CPU @ 2.40GHz, 4085/16342 MB allocatable, 8MCU
Warnings and errors when running hashcat
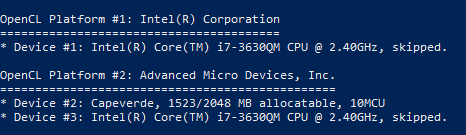
Immediately upon starting the benchmark, errors can offset to exist output. For case:
* Device #iii: Not a native Intel OpenCL runtime. Expect massive speed loss. You lot tin use --force to override, but exercise not written report related errors.
The mistake says that information technology is non the native runtime environs of OpenCL that is used, and a pregnant speed loss is expected. For this reason, OpenCL devices will exist skipped (in the screenshot below it is visible by the word 'skipped'). If we want to utilize them anyhow, nosotros demand to add the --strength option.
Running a benchmark with two options:
.\hashcat.exe -b --force
If you however miss some devices, then you can add one more option -D. After this choice, you need to add together a digit or digits indicating the type of device:
# | Device Type ===+============= ane | CPU 2 | GPU 3 | FPGA, DSP, Co-Processor
Pay attention to a very of import point: an uppercase letter is used for the option. Options are example sensitive. An capital letter letter may take another, fifty-fifty completely different meaning than lowercase letter.
So, 1 is the central processor, and 2 is the graphics processor, then the full command, forth with the selection of all devices bachelor for me, will look like this:
.\hashcat.exe -b --force -D 1,2
The hashcat GUI
In that location are no official graphical interfaces for hashcat. Nevertheless, there are several interfaces that were created by enthusiasts. The well-nigh relevant is this: https://world wide web.hashkiller.co.uk/hashcat-gui.aspx
To install the hashcat GUI, download the archive from the page to which the link above is linked.
Unzip the downloaded archive, information technology already includes:
- hashcat-utils-1.0
- cap2hccap
Requirements for the hashcat GUI:
- simply Windows operating organisation
- dotNET Framework: v4
- hashcat version iii.00 or afterwards
Hashcat you need to download separately, as shown above. Also you need to have the necessary drivers installed.
After you unpack the Hashcat GUI and Hashcat itself, you demand to move the Hashcat folder to the Hashcat GUI binder. Information technology should look similar the following folder structure:
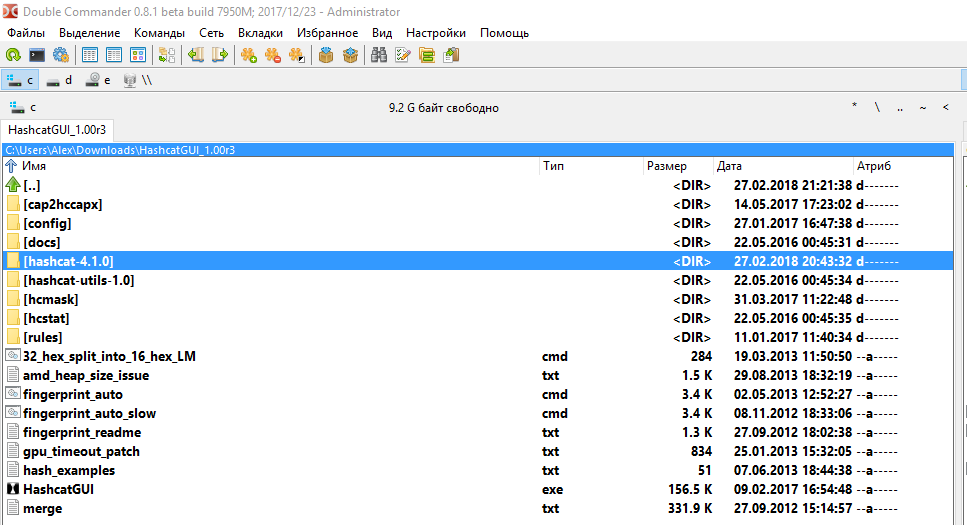
The folder with Hashcat-hashcat-iv.1.0 is highlighted. Note that you do non need to rename the directory with a hashcat.
Double-click the HashcatGUI.exe file to start the plan. Await at the Hashcat GUI:
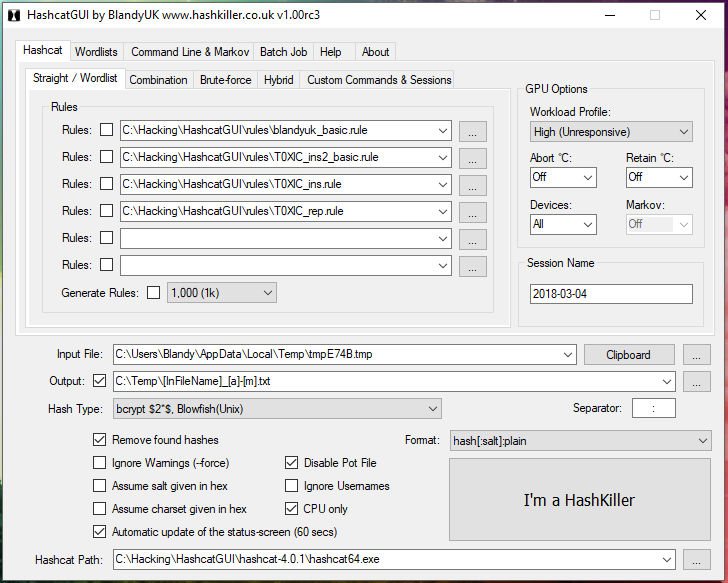
In my opinion, information technology is complicated. In my subjective sense, it is easier to achieve the desired consequence in the command line than in the graphical interface, in which, by the manner, some features are missing.
Moreover, without understanding the concepts of Hashcat, it's unlikely that you lot will be able to do something even in the graphical interface. Therefore, go on reading this article, and we will return to the graphical interface afterward the pages of the miloserdov.org web-site.
How to use hashcat
The programme runs as follows:
hashcat [options]... hash|hashfile|hccapxfile [dictionary|mask|directory]...
Here hashcat is the name of the executable file, in my examples it is .\hashcat.exe.
Divided by the space, options follow the executable file.
The symbol | (piping) in this case ways logical 'OR'. Therefore, hash, OR file with a hash, OR file hccapx file follows after the options. And then dictionary OR mask OR directory follows the hash, depending on the chosen set on.
Consider the use of the program on specific examples. Suppose we have a hash of 53ab0dff8ecc7d5a18b4416d00568f02, which must exist cracked. This hash is known to have been obtained with the MD5 hash algorithm (i.east. it is MD5 hash). It is also known that the encrypted string consists of only small messages of the English language alphabet and has a length of six to 10 characters.
Side by side, nosotros volition show you how to launch a password attack using a multifariousness of tricks.
Specifying the hash type
Different hashes are computed using unlike algorithms. Similarly, their corking is performed using different algorithms. In lodge to correctly launch an assail in Hashcat, y'all must specify the type of attacked hash. To do this, use the -m option, subsequently which yous must specify a number respective to the selected hash blazon.
In the baseline, nosotros are given that the provided hash is MD5. Then on the page https://en.kali.tools/?p=155 we are looking for 'MD5':

Reverse the found hash, look at the cavalcade '#', i.eastward. number. In this case, this number is '0'.
So, to the Hashcat launch control, you need to add -1000 0, it is the option and its value.
If we were given a SHA1 hash, then its number would be 100 and to the Hashcat launch control we would add together -thousand 100 and similarly for any other algorithm.
Typically, a hash type is known from the source where this hash was obtained. In case the type of attacked hash is not known reliably, y'all can endeavor to guess it with the assist of specialized tools.
Hashcat Assault Modes
Hashcat supports various attack modes, the nigh common are:
- Lexicon attack when a list of words is used as password candidates
- Mask attack (brut-force), when candidates in passwords are generated based on the described criteria.
Apply the -a choice to specify the assault way. With it, you can specify whatever type of attack supported in Hashcat, the most popular is a dictionary assault which is indicated by the number 0, and a mask attack (brute forcefulness) which is indicated by the number 3.
And then if nosotros run a dictionary set on, and then we specify -a 0, and if we run mask assail, then nosotros specify -a 3.
Dictionary Attack in Hashcat
The attack starts with the dictionary as follows:
hashcat [options] hash|hashfile|hccapxfile path_to_dictionary
To fissure our hash, create a small dictionary: an ordinary text file named dictionary.txt and copy into it:
00001080 00001111 85be028 85cheyenne 85e6196a 85gpn aaaa1111 aaaa1113 aaaaa aaaaaa aaaaaa1 aaaaaa55 aaaaaaA1 aaaaaaa aaaaaaa7 aaaaaaaa aaaaaaaaaa aaabbb aaabbbc aaasss aaawin aab aabbccdd dancing2009 danciotu dandan1243 dandan44 dandans dandik06 dandy dandy624 hackware nord8899 nordeng86 norderst nordikmix nordmann25 nordrein nordvik81 nordwich yw123123 yw19920 ywa5115 ywab1402 ywhjia4f ywidv ywj7516 ywjpheej
Annotation: By the fashion, with Hashcat comes with an case of a lexicon, it's called example.dict.
So, at this stage nosotros have everything you need to launch an dictionary attack. We collect everything together:
.\hashcat.exe -thou 0 -a 0 53ab0dff8ecc7d5a18b4416d00568f02 lexicon.txt
Here:
- .\hashcat.exe is a executable file
- -m 0 is an option that sets the MD5 hash blazon
- -a 0 is an pick, which value triggers a lexicon attack
- 53ab0dff8ecc7d5a18b4416d00568f02 is a hash to be cracked
- dictionary.txt is a path to the dictionary file.
Since the dictionary is very pocket-size, the program will stop its work very apace:
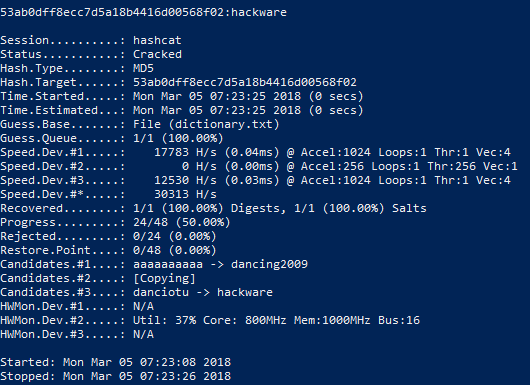
The result of the program:
53ab0dff8ecc7d5a18b4416d00568f02:hackware Session..........: hashcat Status...........: Cracked Hash.Type........: MD5 Hash.Target......: 53ab0dff8ecc7d5a18b4416d00568f02 Fourth dimension.Started.....: Mon Mar 05 07:23:25 2022 (0 secs) Fourth dimension.Estimated...: Mon Mar 05 07:23:25 2022 (0 secs) Judge.Base.......: File (dictionary.txt) Approximate.Queue......: ane/1 (100.00%) Speed.Dev.#one.....: 17783 H/south (0.04ms) @ Accel:1024 Loops:1 Thr:ane Vec:4 Speed.Dev.#two.....: 0 H/s (0.00ms) @ Accel:256 Loops:1 Thr:256 Vec:1 Speed.Dev.#3.....: 12530 H/due south (0.03ms) @ Accel:1024 Loops:1 Thr:1 Vec:4 Speed.Dev.#*.....: 30313 H/s Recovered........: ane/1 (100.00%) Digests, 1/1 (100.00%) Salts Progress.........: 24/48 (50.00%) Rejected.........: 0/24 (0.00%) Restore.Point....: 0/48 (0.00%) Candidates.#ane....: aaaaaaaaaa -> dancing2009 Candidates.#2....: [Copying] Candidates.#iii....: danciotu -> hackware HWMon.Dev.#1.....: N/A HWMon.Dev.#2.....: Util: 37% Core: 800MHz Mem:1000MHz Bus:16 HWMon.Dev.#3.....: Due north/A
The outset line is 53ab0dff8ecc7d5a18b4416d00568f02: hackware contains the attacked hash and subsequently the colon the hacked password, in this case it is hackware.
On the successful hacking says the Status ………..: Cracked line
Hash does not need to be specified in the control line, it can be written to a file, then when the attack is launched, the path to the file containing the hash is specified. For example, create a hashmd5.txt file and copy into it 53ab0dff8ecc7d5a18b4416d00568f02.
Then the control to run will be:
.\hashcat.exe -one thousand 0 -a 0 hashmd5.txt dictionary.txt
The command contains the same options as the previous one, but instead of directly hash, nosotros specified the path to the file containing the hash to fissure.
Annotation: since for educational purposes nosotros fissure the same hash in different ways, in case you echo the examples, you will see the message:
INFO: All hashes constitute in potfile! Use --show to display them.
It means that the hash that yous are trying to fissure has already been cracked earlier. All compromised hashes are stored in the hashcat.potfile file in the same directory equally Hashcat. This is a evidently text file, you lot can open information technology and see the contents, in my case it's:
53ab0dff8ecc7d5a18b4416d00568f02:hackware
This file can be deleted to start attack afresh on the same hash in different ways.
There is likewise the selection --show, after which you need to specify the hash of involvement:
.\hashcat.exe --show 53ab0dff8ecc7d5a18b4416d00568f02
and if it is institute in the hashcat.potfile file, then information about the cracked password will be displayed.
Mask attack in hashcat (animal-force attack in hashcat)
In Hashcat there is no such mode as brut-forcefulness. He was assimilated past the mask assault. This is a more than flexible type of assault, which allows you lot to implement brut-force through finely tuned criteria.
In general, the mask assail has the following form:
hashcat [options]... hash|hashfile|hccapxfile mask
Therefore, information technology is like to the previous i, but instead of the dictionary a mask is indicated.
How to make masks in Hashcat
For composing masks, grapheme sets are used. The character sets in Hashcat come in 2 flavors:
- Built-in Charsets
- User-defined Charsets
Let's begin our acquaintance with the built-in charsets, for many cases, they are enough.
? | Charset ===+========= 50 | abcdefghijklmnopqrstuvwxyz u | ABCDEFGHIJKLMNOPQRSTUVWXYZ d | 0123456789 h | 0123456789abcdef H | 0123456789ABCDEF s | !"#$%&'()*+,-./:;<=>?@[\]^_`{|}~ a | ?l?u?d?s b | 0x00 - 0xff The offset cavalcade denotes a symbolic symbol set. For apply in masks, a question mark must be placed before this designation. For case, ?u means all uppercase messages,?d means all digits.
Suppose we know that the password consists of four characters, the first ii characters are uppercase messages, and the third and fourth characters are digits, then the mask will be every bit follows:
?fifty?l?h?h
To crack the password from our hash given every bit an example, nosotros demand to create a mask consisting of eight characters, each of which is a small letter. This is the mask: ?l?l?l?50?fifty?fifty?l?l
.\hashcat.exe -m 0 -a iii 53ab0dff8ecc7d5a18b4416d00568f02 ?l?l?l?50?l?50?l?l
Here:
- .\hashcat.exe is an executable file
- -m 0 is an option that sets the MD5 hash type
- -a 3 is an option, which value triggers the mask attack
- 53ab0dff8ecc7d5a18b4416d00568f02 is a hash to exist croaky
- ?50?fifty?l?fifty?l?l?l?l is a mask that specifies the generation of eight-grapheme passwords consisting of small messages.
Less than a minute later the password was successfully cracked:
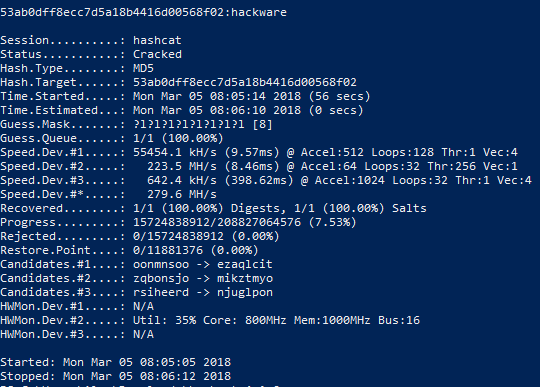
Pay attending to the line:
Progress.........: 15724838912/208827064576 (vii.53%)
That is, 15724838912 variants of passwords from 208827064576 of the total number of variants were tested.
Mask for unknown password length
The password length is not ever known exactly. Even by the condition of our task, the password has a length of 6 to ten characters.
In order to generate passwords of unlike lengths, the following options are bachelor:
Options Brusk / Long | Type | Description | Example -i, --increment | | Enable mask increment way | --increment-min | Num | Get-go mask incrementing at Ten | --increment-min=four --increment-max | Num | Stop mask incrementing at X | --increment-max=8
The -i option is optional. If it is used, it means that the length of candidates for passwords should not be fixed, it should increment past the number of characters.
The --increment-min option is also optional. It determines the minimum length of candidates for passwords. If the -i pick is used, the --increment-min value is ane by default.
And the --increase-max option is optional. It determines the maximum length of candidates for passwords. If the -i choice is specified, but the --increment-max option is omitted, then its default value is the mask length.
Rules for using mask increment options:
- Earlier using --increment-min and --increase-max, you must specify the -i option
- the value of the --increment-min option can be less than or equal to the value of the --increase-max selection, just can not exceed it
- the length of the mask can exist larger in the number of characters or equal to the number of characters specified by the --increment-max option, but the mask length tin non be less than the character length set by --increment-max.
Then, we will correct the launch command for our task (the countersign has a length of half dozen to x characters):
.\hashcat.exe -chiliad 0 -a 3 -i --increment-min=6 --increase-max=10 53ab0dff8ecc7d5a18b4416d00568f02 ?l?l?l?l?fifty?50?l?l?l?l
This control is similar to the previous 1, but three new options have been added (explained just above):
- -i
- --increment-min=6
- --increment-max=10
And also the mask length is increased to 10 characters: ?50?50?l?fifty?l?fifty?fifty?l?l?l (every bit required by the rules for using increment options).
Information technology took a bit more than time to complete the search, as candidates in passwords of 6 (+i seconds on my gland) and 7 symbols (+22 seconds) were tested in add-on:
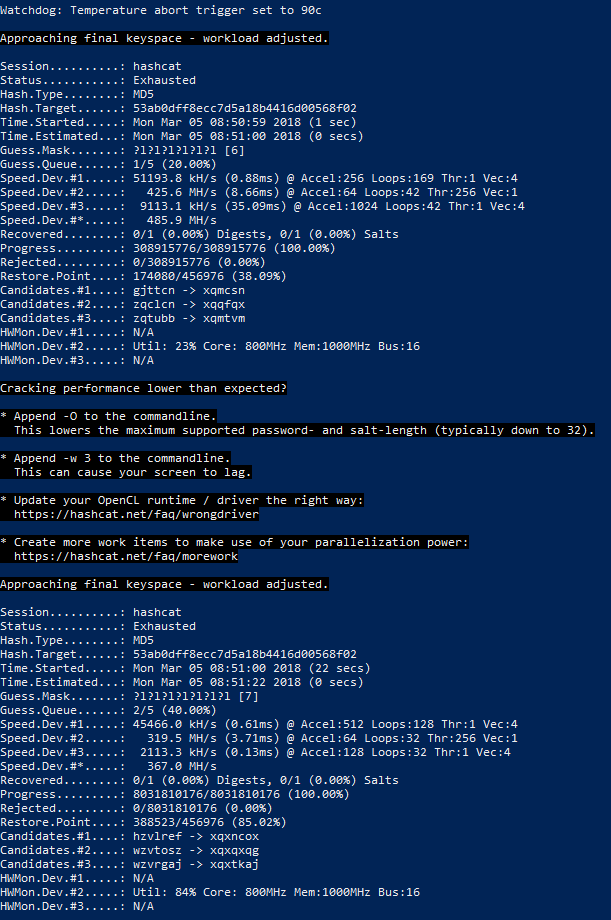
Note the new value of the Condition line:
Condition...........: Wearied
It means that all the password candidates was tested, but none proved true.
Password cracking when some characters are known
There are situations when some of the password symbols are known. For example, nosotros are given the same hash 53ab0dff8ecc7d5a18b4416d00568f02 and somehow we got to know that the beginning iii characters in the password are 'hac'. Then you can specify these characters direct in the mask:
hac?l?fifty?l?l?l?50?fifty
The control is:
.\hashcat.exe -m 0 -a three -i --increment-min=6 --increment-max=10 53ab0dff8ecc7d5a18b4416d00568f02 hac?l?l?l?l?l?fifty?l
Known symbols tin exist placed anywhere in the mask: in the start, in the center, in the finish; these tin exist unmarried characters or groups of characters.
User-defined Charsets in Hashcat
Above, already listed are built-in character sets, which are usually enough. Even so, y'all can specify up to iv of your own custom sets.
Suppose we know that the first three characters in the countersign are digits, and not all, but only numbers from 0 to 4, the fourth character is only uppercase letters, and the fifth and sixth characters are the letters from a to h, besides as the numbers from 5 up to 9.
If in the mask for the first three characters we just indicate the numbers, so obviously not suitable candidates for passwords (containing in the first three positions the numbers that are not in the range from 0 to 4) will be too tested. Nosotros must exclude obviously inappropriate passwords. This can exist washed using custom character sets.
In that location are four user-defined character sets in total. They are specified in options and denoted by numbers. Only in the options, a hyphen is placed before the digit (for example, the showtime user set is -1), and a question mark is placed in the mask earlier the digit (for example, the employ of symbols from the kickoff user set is ?1).
And so, to solve the problem, nosotros start past setting the required number of user sets in the options. These sets tin consist of directly listed characters, you can too utilise built-in character sets, for case ?fifty or ?d or ?u (in whatever combination).
The first custom character set for our task (only numbers from 0 to 4):
-ane 01234
The 2nd user-defined character fix (messages from a to h, as well equally numbers from 5 to 9)
-two abcdefgh56789
Allow me remind you - custom character sets are written among the options (before the mask and before the hash).
Now create a mask (the first three characters in the password are numbers, non all, but simply the numbers from 0 to 4, the quaternary character is only uppercase letters, and the fifth and sixth characters are the letters from a to h, besides every bit the numbers from 5 to nine):
?1?ane?ane?u?2?2
We will disassemble the mask:- the first iii characters are designated as ?1?i?1 (these are units, and not a lowercase alphabetic character L, they are digits 'i') are symbols from the starting time user set. Adjacent goes ?u, this is a congenital-in grapheme set, denoting merely capital messages. The next ii characters are designated as ?2?2, these are symbols from the second user fix.
When specifying custom sets, you can use the annotation of built-in character sets, for instance:
-1 ?l?u
denotes the first user fix consisting merely of large and pocket-sized Latin messages.
And
-1 ?l?u?d
means the starting time user fix consisting only of big and small Latin letters, likewise as numbers.
Every bit already shown above, you lot tin can utilise custom and built-in character sets in any combination in the mask.
How to prove passwords (create a lexicon) in Hashcat without launching a cracking
After creating complex masks, peculiarly with the apply of custom grapheme sets, we would like to bank check whether we did everything correctly. Also, cheers to the flexibility of the Hashcat syntax, it is convenient to utilise it for generating dictionaries by any criteria.
In order to only show passwords without starting great, the --stdout option is used. This option requires -a 3 (masd set on mode). Since cracking does non offset in this example, you do not demand to specify any hashes.
An example of generating passwords for the above-mentioned chore (it is known that the commencement 3 characters in the countersign are numbers, not all, just only numbers from 0 to 4, the fourth character is only uppercase messages, and the fifth and 6th characters are the letters from a to h, too as numbers from 5 to 9):
.\hashcat.exe --stdout -a three -1 01234 -two abcdefgh56789 ?1?1?1?u?2?2
Since many passwords volition be created (more than half a million), instead of displaying on the screen, they tin exist saved to a file. To do this, later the principal control, y'all demand to put the symbol > (means redirecting the output to a file) and write the file name. For instance, to save all passwords to the lab1.dic file, which will be created in the aforementioned folder every bit the executable hashcat.exe:
.\hashcat.exe --stdout -a 3 -1 01234 -2 abcdefgh56789 ?1?ane?1?u?2?2 > lab1.dic
How to create a mask if nothing is known almost the password
If you do not know what characters are in the password, every bit well as how long it is, you have to go through all possible password candidates.
Three assumptions tin can be conditionally distinguished:
- The password can incorporate any numbers, also as upper and lower example letters.
- The password can contain any numbers, uppercase and lowercase letters, as well as other symbols (periods, dashes, commas, quotes, spaces, percent signs, hash marks, etc.)
- The password tin can contain whatsoever numbers, uppercase and lowercase letters, other symbols (periods, dashes, commas, quotes, spaces, pct signs, hash marks, etc.), as well as letters of national alphabets (Cyrillic, hieroglyphs, etc.).
What is the problem with asking search for a password for all characters at once? Let's turn to the formula for the number of possible combinations:
number of characters(password length)
That is, the number of possible characters in the password to the ability of a number, which is the length of the countersign. Moreover, if we practise non know the length, then it is necessary to animal-force
(number of characters)ane + (number of characters)2 + (number of characters)3 + (number of characters)iv + (number of characters)v + …
That is, y'all need to iterate over all passwords that are i graphic symbol long, then all passwords that are ii characters long, and and then on.
In exercise, for many cracking algorithms, this means that it is impossible to guess the password in a reasonable time.
Therefore, if you accept no idea almost the password, then perhaps y'all can commencement with a dictionary attack. It may plow out to be more than efficient than waiting billions of years for brute-force passwords.
Nevertheless, if you need to run a animal-force attack, when the countersign tin can contain upper-case letter and lowercase Latin letters, equally well as numbers and password length from 1 to 12, then you need to utilize the following options and mask:
-i --increase-min=1 --increment-max=12 -one ?l?u?d ?1?i?ane?ane?ane?1?1?1?1?1?1?1
To list all password candidates or shop them in a lexicon:
hashcat --stdout -a 3 -i --increment-min=1 --increase-max=12 -ane ?50?u?d ?i?one?one?one?i?1?1?ane?1?1?1?1
If you lot need to run a brute-force attack when the countersign tin contain capital and lowercase Latin letters, numbers, and symbols !"#$%&'()*+,-./:;<=>?@[\]^_`{|}~ and the countersign length is from i to 12, then y'all need to use the following options and mask:
-i --increment-min=1 --increment-max=12 ?a?a?a?a?a?a?a?a?a?a?a?a
To list all password candidates or shop them in a dictionary:
hashcat --stdout -a 3 -i --increment-min=ane --increase-max=12 ?a?a?a?a?a?a?a?a?a?a?a?a
Samples of hashes
The Hashcat program includes not only assist, but besides hash examples. They can exist useful if you have difficulty in correctly writing the hash format.
To display all examples of hashes at once, run the program with the option --example-hashes:
.\hashcat.exe --case-hashes
You can see a sample of one particular hash. For example, I need to find out what a hash looks similar to crack the RAR5 password; and so I plow to the help page of the program https://en.kali.tools/?p=1558 and search for RAR5 (utilize CTRL+f). I detect that the number of this hash is 13000; Adjacent, I run the programme with the pick --example-hashes and the already-known option -m (after which the hash mode number is specified)
.\hashcat.exe --instance-hashes -one thousand 13000
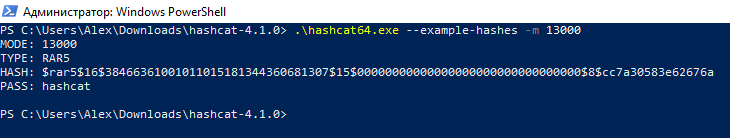
And then, to crack passwords from RAR5 archives, the hash should wait like:
$rar5$16$38466361001011015181344360681307$xv$00000000000000000000000000000000$8$cc7a30583e62676a
Source: https://miloserdov.org/?p=953
Posted by: bartelfeweake95.blogspot.com


0 Response to "How To Install Hashcat On Kali Linux"
Post a Comment